Let’s go through the entire Tailscale system from bottom to top, the same way we built it (but skipping some zigzags we took along the way). With this information, you should be able to build your own Tailscale replacement… except you don’t have to, since our node software is open source and we have a flexible free plan.
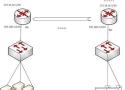
how easy it is to set up an IP tunnel between two locations. This will allow you to access files on a server and share printers between two locations, no matter how far apart. In addition, it enhances data security by encrypting packets as they travel through the tunnel. To accomplish this task, you will need two Mikrotik routers, one at each location, and two public IP addresses.
While having a rugged router at the core of your network is highly recommended, the security settings required to keep the network behind it fully secured can never be over emphasized. In this post, we will look at 9 settings required on a Mikrotik router to keep the network secured.
We can redirect dns requests on Mikrotik to the IP address on the LAN interface of the Mikrotik router, assuming we want the Mikrotik router to serve as the dns server for all connected LAN users, or to the IP address of a locally hosted dns server. There are many reasons for doing this; top most on the list is security.
A. Force Redirect to OPENDNS (without PI hole)
/ip dns
set allow-remote-requests=yes servers=208.67.222.222,208.67.220.220
/ip nat
add action=redirect chain=dstnat dst-port=53 in-interface-list=LAN protocol=tcp
add action=redirect chain=dstnat dst-port=53 in-interface-list=LAN protocol=udp
B. Force OPEN DNS (via PI hole)
/ip firewall nat
add chain=dstnat in-interface-list=LAN protocol=tcp dst-port=53 action=dst-nat to-addresses=10.0.0.31 to-ports=53
add chain=dstnat in-interface-list=LAN protocol=udp dst-port=53 action=dst-nat to-addresses=10.0.0.31 to-ports=53
add chain=srcnat src-address=10.0.0.0/24 dst-address=10.0.0.0/24 action=masquerade
No patch yet for unauthenticated code-execution bug in Palo Alto Networks firewall. //
beheadedstraw Ars Centurion 8y 373
cyberfunk said:
I find this article quite difficult to comprehend, we go from rooting firewalls to somehow magically obtaining Microsoft active directory secrets?There’s no logical flow to how attackers are jumping around the network here and it just feels like bits and pieces of the security reports are copy and pasted here into the article without explanation. I think a better job needs to be done explaining the logical flow events here
The vast majority of firewalls have service accounts with full read access to AD for authentication, usually for VPN's. Microsoft still uses NTLM/NTLMv2 to encrypt their passwords, which is highly susceptible to simple brute force attacks because they don't use salts.
Regardless this is basically the worst of the worst case scenarios for a shitload of Fortune 500 companies, which is what Palo Alto caters to. //
fsck! Ars Centurion
12y
242
Having gone through the Ivanti ordeal as well, I can say AD integration isnt to be taken lightly. From a recovery standpoint, you are now not only looking at VPN remediation but also your entire AD... //
Focher Ars Scholae Palatinae
17y
1,054
KingKrayola said:
We're neither using a PAN firewall nor a blue-chip company.Does using RADIUS for VPN auth provide a level of protection vs direct AD Access, or is it just a case of choosing one's poison?
That depends. RADIUS has a fully configurable authentication mechanism, but if you’re using a flavor of Active Directory then you’re subject to much of the same. Why certificates aren’t a required layer in environments continues to surprise me. I’m not suggesting other laypersons should have it but even I use it on my own network so it’s definitely manageable. //
pnellesen Ars Scholae Palatinae
12y
1,035
Subscriptor++
This kind of news never comes out on a Monday morning, does it? //
With this online TCP port scanner you can scan an IP address for open ports.
OpenWrt, the open source firmware that sprang from Linksys' use of open source code in its iconic WRT54G router and subsequent release of its work, is 20 years old this year. To keep the project going, lead developers have proposed creating a "fully upstream supported hardware design," one that would prevent the need for handling "binary blobs" in modern router hardware and let DIY router enthusiasts forge their own path. //
Failing an image of the proposed reference hardware by the OpenWrt group, let us gaze upon where this all started: inside a device that tried to quietly use open source software without crediting or releasing it.
IPFW is included in the basic FreeBSD install as a separate run time loadable module. The system will dynamically load the kernel module when the rc.conf statement firewall_enable=”YES” is used.
When it comes to choosing a firewall technology for your operating system, the options can be overwhelming. This is particularly true for Linux and FreeBSD, which offer multiple choices. In this article, we’ll take a closer look at four of the most popular firewall options for both systems: iptables, nftables, ipfw, and pf, to help you make an informed decision.
So here’s our contribution to the effort, this article is essentially your four-way comparison of iptables, nftables, IPFW and PF
# pfctl -f /etc/pf.conf && sleep 60 && pfctl -dLoads the ruleset, sleeps for 60 seconds then disables the firewall. Should be enough time to test. If you happen to lock yourself out wait 60 seconds and the firewall will be disabled allowing you access again.
UFW, or Uncomplicated Firewall, is a simplified firewall management interface that hides the complexity of lower-level packet filtering technologies such as iptables and nftables. If you’re looking to get started securing your network, and you’re not sure which tool to use, UFW may be the right choice for you.
This tutorial will show you how to set up a firewall with UFW on Debian 10.
all the tags from https://b.plas.ml
1st-amendment 2nd-amendment 4th-amendment 5th-amendment 9/11 a8 abortion acl adhd afghanistan africa a/i air-conditioning amateur-radio amazon america american android animals anti-americanism antifa anti-semitism antiv antivirus aoip apollo apple appliances archaeology architecture archive art astronomy audio automation avatar aviation backup bash batteries belleville bible biden bill-of-rights biology bookmarks books borg bush business calibre camping capitalism cellphone censorship chemistry children china christianity church cia clinton cloud coldwar communication communist composed computers congress conservatives constitution construction cooking copyleft copyright corruption cosmology counseling creation crime cron crypto culture culture-of-death cummins data database ddt dd-wrt defense democrats depression desantis development diagrams diamonds disinformation diy dns documentation dokuwiki domains dprk drm drm-tpm drugs dvd dysautonomia earth ebay ebola ebook economics education efficiency electricity electronics elements elwa email energy engineering english environment environmentalism epa ethernet ethics europe euthanasia evolution faa facebook family fbi fcc feminism finance firewall flightsim flowers fonts français france fraud freebsd free-speech fun games gardening genealogy generation generators geography geology gifts git global-warming google gop government gpl gps graphics green-energy grounding hdd-test healthcare help history hollywood homeschool hormones hosting houses hp html humor hunting hvac hymns hyper-v imap immigration india infosec infotech insects instruments interesting internet investing ip-addressing iran iraq irs islam israel itec j6 journalism jumpcloud justice kindle kodi language ldap leadership leftist leftists legal lego lgbt liberia liberty linguistics linux literature locks make malaria malware management maps markdown marriage mars math media medical meshcentral metatek metric microbit microsoft mikrotik military minecraft minidisc missions moon morality mothers motorola movies mp3 museum music mythtv names nasa nature navigation navy network news nextcloud ntp nuclear obama ocean omega opensource organizing ortlip osmc oxygen paint palemoon paper parents passwords patents patriotism pdf petroleum pets pews photography photo-mgmt physics piano picasa plesk podcast poetry police politics pollution pornography pots prayer pregnancy presentations press printers privacy programming progressive progressives prolife psychology purchasing python quotes rabbits rabies racism radiation radio railroad reagan recipes recording recycling reference regulations religion renewables republicans resume riots rockets r-pi russia russiagate safety samba satellites sbe science sci-fi scotus secularism security servers shipping ships shooting shortwave signal sjw slavery sleep snakes socialism social-media software solar space spacex spam spf spideroak sports ssh statistics steampowered streaming supplement surveillance sync tarsnap taxes tck tds technology telephones television terrorism tesla theology thorium thumbnail thunderbird time tls tools toyota trains transformers travel trump tsa twitter typography ukraine unions united.nations unix ups usa vaccinations vangelis vehicles veracrypt video virtualbox virus vitamin vivaldi vlc voting vpn w3w war water weather web whatsapp who wifi wikipedia windows wordpress wuflu ww2 xigmanas xkcd youtube zfs