Netinstall is a tool for installing and reinstalling MikroTik devices running RouterOS. Always try using Netinstall if you suspect that your device is not working properly. The tool is available for Windows (with a graphical interface) and for Linux (as a command line tool).
In short, the Netinstall procedure goes like this: Connect your PC directly to the boot port (Usually Ether1, the port labeled BOOT or as otherwise indicated in the product manual) of the device you will be reinstalling. Turn on the device while holding the reset button until it shows up in the Netinstall tool.
Careful. Netinstall re-formats the system's drive, all configuration and saved files will be lost. Netinstall does not erase the RouterOS license key, nor does it reset RouterBOOT related settings, for example, CPU frequency is not changed after reinstalling the device.
///
Traffic graphs will be deleted. Backup and restore if this history is desirable.
RouterBOOT reset button has three functions:
- Hold this button during boot time until the LED light starts flashing, and release the button to reset the RouterOS configuration (total 5 seconds)
- Keep holding for 5 more seconds, LED turns solid, release now to turn on CAPs mode (total 10 seconds)
- Or Keep holding the button for 5 more seconds until the LED turns off, then release it to make the RouterBOARD look for Netinstall servers
AP modes (advanced wireless settings):
- ap-bridge - Basic access point mode.
- bridge - Same as ap-bridge, but limited to one associated client.
- wds-slave - Same as ap-bridge, but scan for AP with the same ssid and establishes WDS link. If this link is lost or cannot be established, then continue scanning. If dfs-mode is radar-detect, then APs with enabled hide-ssid will not be found during scanning.
We have setup MikroTik in different environments, its time for us to build IPsec tunnel between two sites where we have MikroTik routers.
The steps below aim to illustrate how to setup a site to site VPN between two Mikrotik devices using WireGuard. Pre-existing local networks and firewalls exist on both R1 and R2. Between R1 and R2 the WireGuard tunnel will use 172.17.0.0/30. R2 has 172.17.0.1 assigned to its WireGuard interface, while R1 has 172.17.0.2 assigned to its WireGuard interface. The network used, or the order in which IP addresses are assigned is not important, however it is considered best practice to use a point to point subnet between peers.
Site to Site WireGuard tunnel
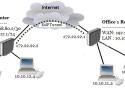
Consider setup as illustrated below. Two remote office routers are connected to the internet and office workstations are behind NAT. Each office has its own local subnet, 10.1.202.0/24 for Office1 and 10.1.101.0/24 for Office2. Both remote offices need secure tunnels to local networks behind routers.
VPN (Virtual Private Network) is a technology that provides a secure tunnel across a public network. A private network user can send and receive data to any remote private network using VPN Tunnel as if his/her network device was directly connected to that private network.
MikroTik provides EoIP (Ethernet over IP) tunnel that is used to create a site to site VPN. EoIP tunneling is a MikroTik RouterOS protocol that creates an Ethernet tunnel between two MikroTik Routers on top of an IP connection. EoIP adds an outer header mentioning the entry point of the tunnel (SourceIP) and the exit point of the tunnel (DestinationIP) but the inner packet is kept unmodified.
Stupid simple setting up WireGuard - Server and multiple peers
jaclaz
Preamble and disclaimer:
The following is a set of Rules that are intended as advice useful to avoid the most common errors observed in configuration posted on this forum.
It is my personal take on the matter, and in no way approved, endorsed or recommended, officially or unofficially, by Mikrotik or their partners or by anyone else.
In other words you are perfectly free to ignore them, though they represent (IMHO) a sort of (good) cheat sheet/reminder for people starting to use these devices.
Experts already know all these issues (and many more) and they already have their own ways to avoid them.
In today's post, we're going to dive into setting up your MikroTik router. I'm working with the MikroTik hAP AX2, but you'll find that these steps are pretty much the same for any MikroTik router.
a practical guide on setting up WireGuard VPN on the MikroTik router.
MikroWizard is designed to help MikroTik users monitor and manage their routers from an IT administrator's viewpoint. Beyond being merely a monitoring and management tool, it functions as a complete management solution that offers PAM-like capabilities specifically for MikroTik devices.
Before developing MikroWizard, which originated from a customer request, I explored existing central management software for MikroTik devices. While "Dude" and other free or commercial tools are available, they didn’t meet my requirements. Many commercial options looked promising but posed security concerns, as trusting a cloud provider to access our network—or relying on the internet for server access—was not an acceptable risk, also they are not offering what I actually looking for.
Here’s what I was searching for MikroTik Managment:
✔ The ability to manage all users who access MikroTik devices, including coworkers, admins, support center staff, customers, and even IT administrators themselves.
✔ A logging system to track all actions performed by admins, customers, and support operators on the router, with historical data showing who made changes and when—similar to the logs provided in PAM solutions.
✔ Centralized creation and editing of system users and groups.
✔ Scheduled firmware updates without requiring internet access on MikroTik routers.
✔ A syslog grabbing and storage feature with filtering and search capabilities.
✔ A centralized, reliable backup solution with differential backups and scheduling options.
Hi All,
I want to set up WireGuard VPN for remote work with 2 MikroTik routers: “home router” and “travel router”. Could you review my hardware and and config?
Requirements:
- “Home router” is connected to the internet in my home
- “Travel router” will be traveling with me.
- It should be possible to connect a “travel router” to any available internet - phone tethering (most often), another router, WIFI
- Traffic from any devices connected to the "travel router" should be visible as traffic from my “home router”.
- “Home router” will be connected to the router with dynamic public IP
8291/tcp Winbox
band (2ghz-b | 2ghz-b/g | 2ghz-b/g/n | 2ghz-onlyg | 2ghz-onlyn | 5ghz-a | 5ghz-a/n | 5ghz-onlyn | 5ghz-a/n/ac | 5ghz-onlyac | 5ghz-n/ac; Default: ) Defines set of used data rates, channel frequencies and widths.
channel-width (20/40/80/160mhz-Ceeeeeee | 20/40/80/160mhz-XXXXXXXX | 20/40/80/160mhz-eCeeeeee | 20/40/80/160mhz-eeCeeeee | 20/40/80/160mhz-eeeCeeee | 20/40/80/160mhz-eeeeCeee | 20/40/80/160mhz-eeeeeCee | 20/40/80/160mhz-eeeeeeCe | 20/40/80/160mhz-eeeeeeeC | 20/40/80mhz-Ceee | 20/40/80mhz-eCee | 20/40/80mhz-eeCe | 20/40/80mhz-eeeC | 20/40/80mhz-XXXX | 20/40mhz-Ce | 20/40mhz-eC | 20/40mhz-XX | 40mhz-turbo | 20mhz | 10mhz | 5mhz; Default: 20mhz) Use of extension channels (e.g. Ce, eC etc) allows additional 20MHz extension channels and if it should be located below or above the control (main) channel. Extension channel allows 802.11n devices to use up to 40MHz (802.11ac up to 160MHz) of spectrum in total thus increasing max throughput. Channel widths with XX and XXXX extensions automatically scan for a less crowded control channel frequency based on the number of concurrent devices running in every frequency and chooses the “C” - Control channel frequency automatically.
First create an interface list for all user/customer interfaces: //
Last, apply the bridge filter to the forward train to catch traffic moving through the bridge.
#this filter rule will block DHCP servers
/interface bridge filter
add action=drop chain=forward in-interface-list=customers ip-protocol=udp mac-protocol=ip src-port=67If the device has a default or existing configuration that requires replacement, it is necessary to initiate a configuration reset.
This involves applying a clean, empty configuration using the command /system/reset-configuration no-defaults=yes, followed by a device reboot. //
For example, load saved configuration file
[admin@MikroTik] > import address.rsc
Opening script file address.rsc
Script file loaded and executed successfully
[admin@MikroTik] >- verbose Reads each line from the file and executes individually, allowing to debug syntax or other errors more easily.
- dry-run Simulates the import without making any configuration changes. This helps in catching syntax errors. This option is only available in verbose mode.
RouterOS allows resetting configuration with /system reset-configuration command //
The backup file of the existing configuration is stored before reset. That way you can easily restore any previous configuration if the reset is done by mistake.
If the router was installed using Netinstall and had a script specified as the initial configuration, the reset command executes this script after purging the configuration. To stop it from doing so, you will have to reinstall the router.
It is possible to override the default reset behavior with the parameters below:
- keep-users Do not remove existing users from the configuration
- no-defaults Do not load the default configuration, just clear the configuration
Depending on the router model, different Quickset modes might be available from the Quickset dropdown menu:
- CAP: Controlled Access Point, an AP device, that will be managed by a centralized CAPsMAN server. Only use if you have already set up a CAPsMAN server.
- CPE: Client device, which will connect to an Access Point (AP) device. Provides option to scan for AP devices in your area.
- HomeAP: The default Access Point config page for most home users. Provides fewer options and simplified terminology.
- HomeAP dual: Dual band devices (2GHz/5GHz). The default Access Point config page for most home users. Provides fewer options and simplified terminology.
- Home Mesh: Made for making bigger WiFi networks. Enables the CAPsMAN server in the router, and places the local WiFi interfaces under CAPsMAN control. Just boot other MikroTik WiFi APs with the reset button pressed, and they will join this HomeMesh network (see their Quick guide for details)
- PTP Bridge AP: When you need to transparently interconnect two remote locations together in the same network, set one device to this mode, and the other device to the next (PTP Bridge CPE) mode.
- PTP Bridge CPE: When you need to transparently interconnect two remote locations together in the same network, set one device to this mode, and the other device to the previous (PTP Bridge AP) mode.
- WISP AP: Similar to the HomeAP mode, but provides more advanced options and uses industry standard terminology, like SSID and WPA.