Urban VPN Proxy targets conversations across ten AI platforms: ChatGPT, Claude, Gemini, Microsoft Copilot, Perplexity, DeepSeek, Grok (xAI), Meta AI.
For each platform, the extension includes a dedicated “executor” script designed to intercept and capture conversations. The harvesting is enabled by default through hardcoded flags in the extension’s configuration.
There is no user-facing toggle to disable this. The only way to stop the data collection is to uninstall the extension entirely.
[…]
The data collection operates independently of the VPN functionality. Whether the VPN is connected or not, the harvesting runs continuously in the background.
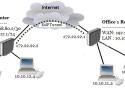
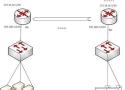
We have setup MikroTik in different environments, its time for us to build IPsec tunnel between two sites where we have MikroTik routers.
The steps below aim to illustrate how to setup a site to site VPN between two Mikrotik devices using WireGuard. Pre-existing local networks and firewalls exist on both R1 and R2. Between R1 and R2 the WireGuard tunnel will use 172.17.0.0/30. R2 has 172.17.0.1 assigned to its WireGuard interface, while R1 has 172.17.0.2 assigned to its WireGuard interface. The network used, or the order in which IP addresses are assigned is not important, however it is considered best practice to use a point to point subnet between peers.
VPN (Virtual Private Network) is a technology that provides a secure tunnel across a public network. A private network user can send and receive data to any remote private network using VPN Tunnel as if his/her network device was directly connected to that private network.
MikroTik provides EoIP (Ethernet over IP) tunnel that is used to create a site to site VPN. EoIP tunneling is a MikroTik RouterOS protocol that creates an Ethernet tunnel between two MikroTik Routers on top of an IP connection. EoIP adds an outer header mentioning the entry point of the tunnel (SourceIP) and the exit point of the tunnel (DestinationIP) but the inner packet is kept unmodified.
Stupid simple setting up WireGuard - Server and multiple peers
Like most well-known remote access tools, NetBird is built on WireGuard, making it fast and known for its security. However, unlike many other remote access tools, it has identity management built into its core. Therefore, when you self-host it, the first thing you set up is Zitadel, the default identity provider. But you can use any IDP that uses OpenID, including Keycloak and Authentik. The cloud-based version supports Google Workspace, Azure, Okta, and Auth0, but this feature is only available behind the Teams' subscription tier. //
Be careful here, though, as it seems the ability to approve peers is limited to the cloud-based version, so you could end up with new users that you don't want. That's possibly okay because new users don't have access to anything unless you've set up access control to allow ALL, which is bad security practice anyway. //
NetBird is a powerful, self-hosted access tool with numerous advanced access control policies that do more than enable NAT traversal for encrypted tunnels, making SSH access to remote web servers easy to set up. You could set up one peer on your home network as a routing peer, potentially on your router, and access internal resources on your network securely. It's also simple to set up site-to-site tunnels, without the complicated firewall configurations you'd typically need. //
You can still use the free cloud-based version for up to 5 users and 100 devices, although you'd lose access to Posture Checks (handy for segmentation) and a few other things.
One one my biggest worries about VPNs is the amount of trust users need to place in them, and how opaque most of them are about who owns them and what sorts of data they retain.
A new study found that many commercials VPNS are (often surreptitiously) owned by Chinese companies.
WireGuard generally doesn’t require any performance tuning to use. It’s been designed to work well on modern network stacks under a variety of different configurations. Sending traffic through its encrypted tunnel requires only a little bit of overhead, in the form of slightly higher CPU and network usage.
That said, there are a few things you can adjust if you are experiencing WireGuard performance issues. This article will walk you through some strategies to Testing and Tuning your WireGuard network performance.
We all know that Dad is the IT infrastructure manager at home, so when it became clear that we needed a VPN for everyone to enjoy that infrastructure (aka access to streaming services) on their phones and laptops when they were away- it became Dad's job to make it happen.
Before we get into what Tailscale is or how it compares to a traditional remote access VPN, let’s take a quick look at Tailscale in action. The main problem Tailscale solves is remote access to your internal workloads.
In my homelab, I have a server running Linux. When I’m on my home network, I can access it directly without any issues. But if I step outside and want to access the same server over the Internet, Tailscale makes that much easier and you can have it up and running in about 10 minutes for free.
The main difference between Tailscale and WireGuard is that WireGuard is a self-hosted VPN server, while Tailscale adds user authentication and device management to the WireGuard VPN Protocol. Tailscale also relies on cloud servers for authentication and connection, while WireGuard is fully self-hosted and only relies on your private server.
Before looking at Tailscale vs. WireGuard more in-depth below, I want to explain exactly what they both are and how they function.
What is Tailscale?
Tailscale is a VPN service that utilizes the WireGuard Protocol. Tailscale allows you to easily create a VPN tunnel with absolutely no port forwarding. For users who have a CGNAT or simply do not feel comfortable port forwarding, Tailscale is one of the easiest ways to configure a VPN tunnel.
It’s also important to know that while Tailscale utilizes the WireGuard Protocol, it does not function the same way that WireGuard does. While they utilize the exact same point-to-point encryption, using Tailscale requires the Tailscale network to be accessible.
Tailscale is a zero-configuration VPN solution that uses WireGuard, an open-source VPN protocol. It focuses on providing an easy-to-use and configure management interface for the WireGuard protocol.
Tailscale is different than WireGuard in many ways, but it’s a better comparison to ZeroTier than WireGuard due to the way that it’s set up and configured, as well as its functionality. //
ZeroTier is a software-defined networking application that allows devices to be connected over a global network with minimal setup and configuration. It’s designed to function similarly to a local area network (LAN) environment, making it seem like all devices are connected to the same network even if they are physically located in different parts of the world.
Hi All,
I want to set up WireGuard VPN for remote work with 2 MikroTik routers: “home router” and “travel router”. Could you review my hardware and and config?
Requirements:
- “Home router” is connected to the internet in my home
- “Travel router” will be traveling with me.
- It should be possible to connect a “travel router” to any available internet - phone tethering (most often), another router, WIFI
- Traffic from any devices connected to the "travel router" should be visible as traffic from my “home router”.
- “Home router” will be connected to the router with dynamic public IP
An open source, self-hosted implementation of the Tailscale control server.
What is Tailscale
Tailscale is a modern VPN built on top of Wireguard. It works like an overlay network between the computers of your networks - using NAT traversal.
Everything in Tailscale is Open Source, except the GUI clients for proprietary OS (Windows and macOS/iOS), and the control server.
The control server works as an exchange point of Wireguard public keys for the nodes in the Tailscale network. It assigns the IP addresses of the clients, creates the boundaries between each user, enables sharing machines between users, and exposes the advertised routes of your nodes.
A Tailscale network (tailnet) is private network which Tailscale assigns to a user in terms of private users or an organisation.
Design goal
Headscale aims to implement a self-hosted, open source alternative to the Tailscale control server. Headscale's goal is to provide self-hosters and hobbyists with an open-source server they can use for their projects and labs. It implements a narrow scope, a single Tailscale network (tailnet), suitable for a personal use, or a small open-source organisation.
WireGuard is an open-source modern VPN (Virtual Private Network) solution that utilizes cryptography protocols to create secure network connections between devices. It's efficient and offers improved reliability than traditional VPN protocols like IPSec. This guide explains how to install WireGuard VPN on a FreeBSD 14.0 and securely configure network tunnels on the server.
But if you happen to have a cloud-based Linux server running anyway, building a WireGuard VPN can be a simple and free way to add some serious, compromise-free security and privacy to your life.
If you plan to limit the VPN to just devices owned by you and a few friends, you'll probably never even notice any extra resource load on your server. Even if you had to fire up and pay for a dedicated AWS EC2 t2.micro reserved instance, the annual costs should still come out significantly cheaper than most commercial VPNs. And, as a bonus, you'll get complete control over your data.
Right now I'm going to show you how all that would work using the open source WireGuard software on an Ubuntu Linux server.
Why WireGuard? Because it's really easy to use, is designed to be particularly attack resistant, and it's so good at what it does that it was recently incorporated into the Linux kernel itself.
The actual work to make this happen really will take only five minutes - or less. Having said that, planning things out, troubleshooting for unexpected problems and, if necessary, launching a new server might add significant time to the project.
This week there was an unfortunate outage on the mynetname.net Dynamic Domain Name Service (DDNS) that MikroTik hosts for free to their customers. Many MikroTik users all over the world rely on this service for remote access to their MikroTik infrastructure. Official documentation is here: https://wiki.mikrotik.com/wiki/Manual:IP/Cloud#DDNS
I thought it would be useful to share what I learned about how RemoteWinBox solves this problem for its customers, so that you too can can roll your own remote access to your MikroTiks!
FreeBSD: Setup SoftEther and configure Offshore 100% Logless VPN server (Windows 10 as clients)
Let’s go through the entire Tailscale system from bottom to top, the same way we built it (but skipping some zigzags we took along the way). With this information, you should be able to build your own Tailscale replacement… except you don’t have to, since our node software is open source and we have a flexible free plan.
how easy it is to set up an IP tunnel between two locations. This will allow you to access files on a server and share printers between two locations, no matter how far apart. In addition, it enhances data security by encrypting packets as they travel through the tunnel. To accomplish this task, you will need two Mikrotik routers, one at each location, and two public IP addresses.