There is no room for looking on Jesus Christ as a martyr; His death was not something that happened to Him which might have been prevented. His death was the very reason why He came.
Never build your preaching of forgiveness on the fact that God is our Father and He will forgive us because He loves us. It is untrue to Jesus Christ’s revelation of God; it makes the Cross unnecessary, and the Redemption “much ado about nothing.” If God does forgive sin, it is because of the Death of Christ. God could forgive men in no other way than by the death of His Son, and Jesus is exalted to be Saviour because of His death. //
Anything that belittles or obliterates the holiness of God by a false view of the love of God, is untrue to the revelation of God given by Jesus Christ. Never allow the thought that Jesus Christ stands with us against God out of pity and compassion; that He became a curse for us out of sympathy with us. Jesus Christ became a curse for us by the Divine decree.
Congress has voted to compel release of the so-called “Epstein files,” a trove of documents amassed during criminal investigations into the sex offender who committed suicide in 2019.
The contents are likely brimming with thousands of names of innocent people, many of whom have provided alibis or were never under any suspicion of sex trafficking or any other crime.
A significant portion of any criminal investigation consists of uncorroborated accusations that are floated by people on the periphery of the case, third-hand accounts, theories and rumors.
We already know Epstein was a vile and depraved criminal. And no one should belittle the experience of his victims.
Anyone, however, can make allegations. Even victims don’t always remember correctly.
This is why grand jury files are almost always sealed.
Things a braggart such as Epstein might have said may not be true.
That’s why we have procedures, the rule of law, statutes of limitations and trials.
Moreover, the Epstein files will be filled with information obtained by law enforcement using warrants based on probable cause signed off by a judge for a specific reason.
The warrants, which allow the use of government coercion, weren’t signed so that the public could have access to the emails of every person Epstein spoke with.
Americans caught up in criminal investigations have a presumption of privacy.
What principle stops a future Congress from cracking open useful Justice Department files and releasing any embarrassing second-hand conversations that involve their political enemies?
If authorities believe that his prosecution in Florida was corrupt, they should launch an investigation into misconduct.
This isn’t an ancient case. Most of the victims are still alive.
Most of the powerful people involved with Epstein are still alive. His sidekick is still alive and in prison.
Investigate.
But much of this is driven by rank partisanship.
Democrats like to act as if Trump is engaged in some coverup.
Well, they had every chance to release the files during Joe Biden’s presidency. I’ve not seen a single Democrat explain why they didn’t.
One suspects that if there was anything implicating Trump of genuine wrongdoing, we’d have seen the files leaked long ago.
House Democrats couldn’t even muster the votes to censure Democratic Virgin Islands Delegate Stacey Plaskett, who exchanged text messages with Epstein during a 2019 congressional hearing.
The whole thing is a farce.
One of the most anxiety-inducing parts of self-hosting for me is ensuring that everything is as locked-down security-wise as possible. That's become even more critical as I increase my footprint, adding my own domain and subdomains that point to each service. I'm also a little particular, and while I could use a self-signed TLS certificate to ensure HTTPS for the services that need it, the reminder that it hasn't been done "properly" every time I access those services irks me.
And while there's any number of reverse proxies that I could use to access those services, few are as easy to set up and use as Caddy. //
Officially, Caddy is an open-source web server that can be used for many things. But because it's so easy to set up and includes built-in automatic HTTPS with TLS certificate management, it's often used as a reverse proxy for the home lab. That's because every domain, IP address, and even localhost are served over HTTPS, thanks to the fully automated, self-managed certificate authority.
The entire server is controlled by a single configuration file, the "Caddyfile," which is human-readable, and most tasks are handled with a few simple lines of text.
NTSB released images showing a UPS plane's engine separation during a Louisville crash.
The Nov. 4 crash killed 14 and left a half-mile debris field.
NTSB found fatigue cracks in engine hardware; investigation continues with final report pending.
The late, great Dr. Petr Beckmann was editor of the great journal Access to Energy, founder of the dissident physics journal Galilean Electrodynamics (brochures and further Beckmann info here; further dissident physics links), author of The Health Hazards of NOT Going Nuclear (Amazon; PDF version) and the pamphlets The Non-Problem of Nuclear Waste and Why “Soft” Technology Will Not Be America’s Energy Salvation. (See also my post Access to Energy (archived comments), and this post.)
I just came across another favorite piece of his and have scanned it in: Economics as if Some People Mattered (review of Small is Beautiful by E.F. Schumacher), first published in Reason (October 1978), and reprinted in Free Minds & Free Markets: Twenty-Five Years of Reason (1993). Those (including some libertarians and fellow travelers) who also have a thing for “smallness” and bucolic pastoralism should give this a read.
Small is Beautiful is the title of a book by E.F. Schumacher. It is also a slogan describing a state of mind in which people clamor for the rural idyll that (they think) comes with primitive energy sources, small-scale production, and small communities. Yet much–perhaps most–of their clamor is not really for what they consider small and beautiful; it is for the destruction of what they consider big and ugly.
… The free market does not, of course, eradicate human greed, but it directs it into channels that the consumer the maximum benefit, for it is he who benefits from the competition of”profit-greedy” businessmen. The idea that the free market is highly popular among businessmen is one that is widespread, but not among sound economists. It was not very popular in 1776, when Adam Smith’s Wealth of Nations was published, and it has not become terribly popular with all of them since–which is not surprising, for the free market benefits the consumer but disciplines the businessman.
If the free market is so popular with business, what are all those business lobbies doing in Washington? The shipping lobby wants favors for U.S. ships; the airlines yell rape and robbery when deregulation from the governmental CAB cartel threatens; the farmers’ lobby clamors for more subsidies. What all these lobbies are after is not a freer market but a bigger nipple on the federal sow.
Petr Beckmann
- Hammer and Tickle Hammer and Tickle $ 12.00
- The Health Hazards of Not Going Nuclear The Health Hazards of Not Going Nuclear $ 15.00
- Access to Energy - 5 Volume Set Access to Energy - 5 Volume Set $ 199.00
- Fancy Napkin Foldings Fancy Napkin Foldings $ 8.00
- Musical Musings Musical Musings $ 20.00
- A History of Pi A History of Pi $ 16.00
- The Non-problem of Nuclear Waste The Non-problem of Nuclear Waste $ 8.00
- Orthogonal Polynomials for Engineers and Physicists Orthogonal Polynomials for Engineers and Physicists $ 39.00
- Radiation by an Antenna With Non-Gaussian Phase Errors Radiation by an Antenna With Non-Gaussian Phase Errors $ 8.00
- Electromagnetic Feilds and VDT-itis Electromagnetic Feilds and VDT-itis $ 8.00
- The Radiation Bogey The Radiation Bogey $ 8.00
This tutorial will guide you through the process of setting up a TLS certificate using acme.sh and IONOS Cloud DNS. By following these steps, you will be able to secure your web server with a valid TLS certificate issued by ZeroSSL.
On a sunny morning on October 19 2025, four men allegedly walked into the world’s most-visited museum and left, minutes later, with crown jewels worth 88 million euros ($101 million). The theft from Paris’ Louvre Museum—one of the world’s most surveilled cultural institutions—took just under eight minutes.
Visitors kept browsing. Security didn’t react (until alarms were triggered). The men disappeared into the city’s traffic before anyone realized what had happened.
Investigators later revealed that the thieves wore hi-vis vests, disguising themselves as construction workers. They arrived with a furniture lift, a common sight in Paris’s narrow streets, and used it to reach a balcony overlooking the Seine. Dressed as workers, they looked as if they belonged.
This strategy worked because we don’t see the world objectively. We see it through categories—through what we expect to see. The thieves understood the social categories that we perceive as “normal” and exploited them to avoid suspicion. Many artificial intelligence (AI) systems work in the same way and are vulnerable to the same kinds of mistakes as a result.
The sociologist Erving Goffman would describe what happened at the Louvre using his concept of the presentation of self: people “perform” social roles by adopting the cues others expect. Here, the performance of normality became the perfect camouflage. //
Iphtashu Fitz Ars Tribunus Militum
18y
1,651
Derecho Imminent said:
It could be argued that people ignored them not because of conformity, but because of class structure.
I think it largely is conformity. There are plenty of other examples of successful crooks/robberies/etc. that took advantage of conformity:
- The Isabella Stewart Gardner Museum art heist started with phony Boston Police officers knocking on the door.
- The Belfast Ireland bank heist in 2004 was similarly perpetrated by phony police officers
- Frank Abignale claims to have impersonated a pilot, a lawyer, and other professions to con people in the 1960s and 70s.
- The Banco Central Heist in Brazil involved a "gardening" business that opened up right next to the bank to hid the digging of a tunnel into the bank. It took 3 months to dig the tunnel.
All of these used social engineering tactics at different levels of class structure to perform their respective robberies. You can find plenty of other robberies along these lines with a little bit of effort.
But vanity plates can get you in trouble. One security researcher found this out when he ordered a plate that read, "NULL" — also the word the computer system entered for a ticket whenever a cop left the license plate field blank. Similar results have happened to drivers who opted for "NO PLATE," "NOTAG," or "VOID." They ended up receiving thousands of dollars in tickets for things they didn't do.
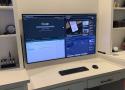
One screen beats four any day
The idea of swapping 4–5 monitors for one huge TV sounded pretty stupid at first. But I can't see myself going back now, though. My computer runs cooler and quieter, my desk isn't buried under stands and cables, and I actually get more done without hunting for windows across different screens. Bigger ended up being better than more. If you're buried in monitors and wires right now, one large display might be the move. It worked for me.
Easy decision. I restored a 1972 VW Beetle convertible. It was a full body and drive train restoration back to what approximated factory new condition. BUT It had drum brakes all around (until I installed a disc brake package on the front end) which were strictly press and pray.
The story goes that, when E.L. Cord purchased a controlling stake in the Duesenberg motor company in 1926, he instructed the Duesenberg brothers to create the finest automobile they knew how to. As a result, the brothers developed the Duesenberg Model J, and while it was impressive in many ways, it was the straight-eight under the hood that stole column inches in the day.
From the 'eight' came 265 horsepower at 4,200 rpm, effectively doubling the grunt on offer from contemporary Cadillac or Packard models, and therefore more than delivering on the brief set by Cord just two years prior. It checked in at 1,150 pounds, and at the time, the Model J's crankshaft retailed for $605 in the parts catalog — more than what a brand-new Model A would set you back. This was anything but a car for the people, and more a statement of sheer excess, with the 419.7ci straight-eight taking center stage.
Very few revisions would be employed over the years, although an 'SJ' variation of the engine did arrive some years later, sporting a supercharger. This addition saw output swell from 265 to 320 horses, and this particular rendition of the Duesenberg would remain America's most powerful road car until the 1950s. It demonstrated just how far ahead of the game the now-defunct Duesenberg automaker was in the late 1920s and early 1930s.
Direct, encrypted file transfers from your computer to anyone, anywhere — no signup, no cloud storage in between.
Think of it like AirDrop for everyone.
GitHub
Free & Open source
Welcome to Boyds Hardwood Gunstocks and thank you for visiting our online hunting tutorial!
Hunting is a popular outdoor activity, with millions of new sportsmen joining its ranks every year. Some people hunt for sustenance, while others pursue game for sport. Either way, many aspiring hunters sometimes find it difficult to break into the pastime, especially if there’s no one to point them in the right direction.
Everyone on the Boyds team believes in giving new hunters a fair shot. With that in mind, we crafted the following compilation of tips and advice for novice outdoorsmen or those otherwise new to the sport. Want to know how to get a hunting license? It’s here. Curious about selecting the right firearm? We got you covered. A bit confused about hunting seasons and where to find a good guide? No problem.
This was a [Solar] company that was not only economically unviable but was also conducting outright shady business practices. ///
That's breaking the laws of physics for a solar company to conduct shady business practices!
The .30-06 Springfield remains one of America's most trusted hunting cartridges. This trajectory chart shows the classic 180-grain load at 2,700 fps with a 100-yard zero, giving you solid data from the muzzle out to 500 yards - perfect for everything from whitetail to elk hunting distances.
Our calculator lets you customize the trajectory for your specific load and conditions. Click "Modify Calculation" below to input your exact bullet weight and velocity. You can adjust for shooting angle, wind conditions, and environmental factors to match your hunting scenario or range session.
The question “How far does a 30-06 bullet travel?” can be answered directly: Under ideal conditions, a 30-06 bullet can travel over 5,000 yards (approximately 2.84 miles). However, the effective range and lethal range are significantly less. //
The 30-06 bullet drop at 500 yards depends on several factors. These include bullet weight, muzzle velocity, and ballistic coefficient. It is often between 30-50 inches.
Nephophobia, or cloud phobia, is an excessive or irrational fear of clouds that can evoke intense emotional responses and substantially impact an individual's overall well-being.
Portable file server with accelerated resumable uploads, dedup, WebDAV, FTP, TFTP, zeroconf, media indexer, thumbnails++ all in one file, no deps
Windows command line utility to compute hash of directories and files - idrassi/DirHash
Possible values for HashAlgo (not case sensitive):
- MD5
- SHA1
- SHA256
- SHA384
- SHA512
- Streebog
- Blake2s
- Blake2b
- Blake3
- Any combination of the above separated by comma, except when -verify is used
If HashAlgo is not specified, Blake3 is used by default.
ResultFileName specifies an optional text file where the result will be appended.